Intel announced today that it will include its Control-Flow Enforcement Technology (CET) hardware-based protection to combat common malware, in its upcoming Tiger Lake mobile CPUs.
Intel has been working on CET for 4 years in collaboration with Microsoft, and this will be the first time we’ll see it in action in Tiger Lake CPUs.
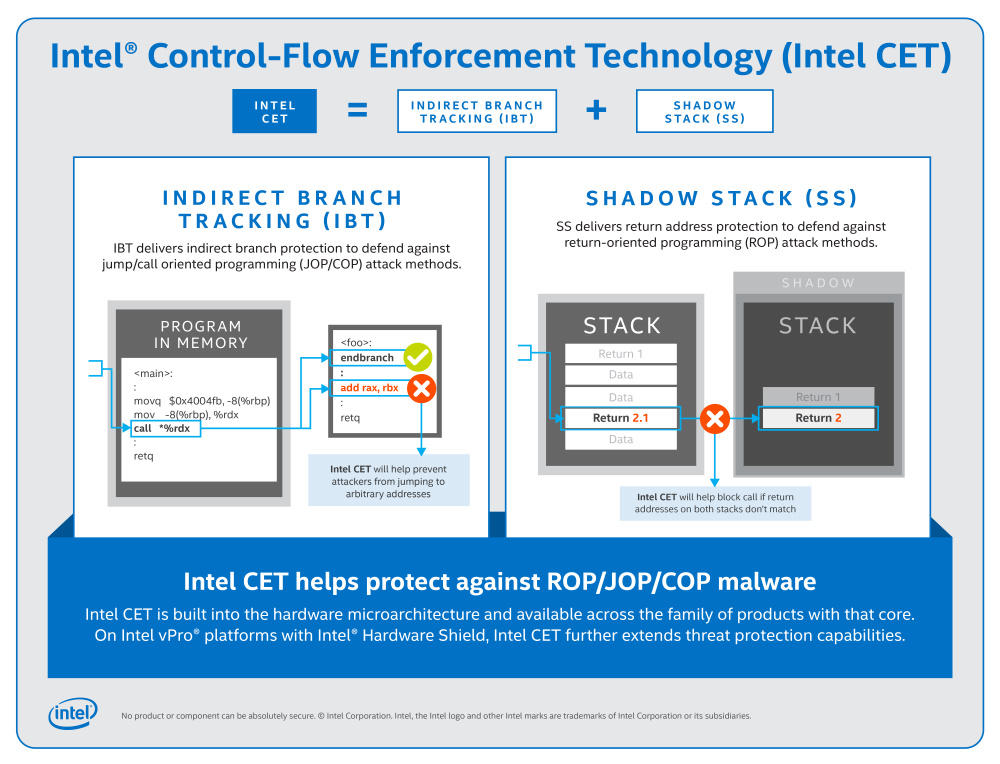
In 2016, the chipmaker company detailed CET. The hardware protection measure will regulate the control flow of operations executed in a CPU. Often, malware writers disturb the control flow of applications by inserting malicious code and running an app over another.
CET aims to restrict meddling with control flow via two different techniques – Indirect branch tracking and shadow stack.
In Indirect branch tracking, certain restrictions are added to the way apps use CPU branch tables. It is a method to transfer program control to another part of a program or a different program.
Indirect Branch Tracking will offer protection against Jump Oriented Programming and Call Oriented Programming, the two most commonly deployed techniques by malware writers to distort the control flow of applications.
Shadow Stack, on the other hand, is a mechanism that creates a duplicate control flow of an app, and stores it in a secured place in CPU that is protected against application code memory access.
The Shadow Stack is intended to offer protection against Return-Oriented Programming, a technique used by malware writers to hijack the intended code of flow of an app.
CET on CPUs will work only when the operating system supports it. Microsoft has already added support for CET in Windows 10 Version 2004. Intel hasn’t announced a release date for Tiger Lake architecture-based CPUs.
This isn’t the first time Intel has adopted a hardware-based approach to tackle persistent malware attacks. Earlier, it baked SGX or Software Guard eXtension in its CPUs. However, it did not offer the results intended by the company.
SGX provides a shielded execution environment called ‘enclaves’ to deal with sensitive data and code. Researchers later discovered a new breed of Spectre-based SGX attack that could compromise data from secure enclaves.
It remains to be seen how effective CET will turn out to be once it’s launched.
The post Intel To Add Anti-Malware Hardware In Its Tiger Lake CPUs appeared first on Fossbytes.
from Fossbytes https://ift.tt/2Y8a3Zj
via IFTTT



0 comments:
Post a Comment